Resisting Cyber Attacks Through Layered Security Systems

Multifactor authentication is a critical cyber defense, yet criminals are working to bypass it. Use these tips to build an effective MFA layer.
Key Takeaways
-
A variety of supplementary security mechanisms, such as multifactor authentication, have risen in popularity and adoption across organizations.
-
Although having MFA systems in place is crucial today, it is not a silver bullet that can protect businesses from all cyber attacks.
-
As attacks evolve, so should your defense. Companies can take various approaches to mitigate the emerging risk of MFA bypass.
Understanding cyber risk, getting better visibility of exposures, and measuring business impact is at the heart of every organization’s cyber security strategy. Defenders and protectors are in a constant game of cat and mouse with threat actors who are relentlessly upping their game when trying to circumvent cyber security systems.
Even people with very little technical ability to design their own cyber attack can do so through Phishing-as-a-service (PhaaS), which provides regular phishing kits for as low as $50 and more sophisticated ones for $900.1
Multifactor Authentication — An Essential Cyber Security Tool
A variety of supplementary security mechanisms, such as multifactor authentication (MFA), have risen in popularity and adoption across organizations. Historically, a combination of a username and a password has been used to secure online resources and accounts. However, a surge in hackers easily getting access to user credentials made it necessary to add more layers of authentication to ensure that accounts remain secured.
“MFA is now a must-have”, says Heidi Wachs, Aon’s Engagement Management managing director for Cyber Solutions. “It is good cyber security hygiene to do so.” In fact, the use of MFA increased by 78 percent in the month of March 2020 alone,2 when people globally started working from home and organizations tried to bolster security on applications that users accessed outside the office.
MFA use Skyrocketed at the Start of the COVID-19 Pandemic

Source: Leading SSO solution provider, Okta
MFA is now a requirement in the UK and EMEA to protect financial data/personal data and ensure compliance with GDPR.3
However, while MFA is mandatory in regulated industries, such as financial institutions and larger multinational companies, it is not always readily implemented in small and medium enterprises. According to CyberEdge’s 2022 Cyberthreat Defense Report (CDR),4 only about half of surveyed companies use MFA.
"Larger organizations are aware due to recommendations from security advisors," says Stephen Morgan, Aon's APAC head of Digital Forensics & Incident Response. "If smaller companies had cyber insurance, their insurer would have advised that they need MFA to even qualify for the insurance in the first place."
Smaller organizations do not have this luxury, Morgan adds. "Due to a lack of dual authentication in their Office 365 environment (email, documents, etc.), such organizations can have poor security," says Morgan. "Exposure to knowledge of cyber security is vital."
As businesses continue to enable a remote workforce, the question on leaders’ minds should not be whether they have implemented MFA but rather how to ensure effective MFA.
When MFA Fails to Protect
Although having MFA systems in place is crucial today, it is not a silver bullet that can protect businesses from all cyber attacks. “Cyber security is a constant game of cat and mouse,” says John Ansbach, Aon’s Engagement Management managing director for Cyber Solutions.
“As more companies implement MFA, threat actors are updating their techniques to get around MFA or find other ways to attack companies with ransomware and compromise business emails,” he adds.
In 2022, threat actors continued to expose the shortcomings of MFA, catapulting terms such as MFA bombing, MFA bypass, and MFA fatigue5 into the cyber security lexicon.
One such threat actor, Lapsus$, bypassed organizations’ MFA frameworks by spamming account holders in 2022. Victims included Microsoft, T-Mobile and Nvidia. A recent PhaaS toolkit dubbed EvilProxy also enabled cyber criminals to attack users with MFA on a broad scale.
In a recent red team exercise, Aon’s Cyber Solutions team was able to use MFA bypass, via social engineering (timing the MFA challenge around the time that people login in) to breach a large investment firm.
Common Forms of MFA Bypass Attacks
- MFA fatigue
- Machine-in-the-Middle attacks
- Token theft
"Our biggest fear with MFA bypass attacks is a user approving a fraudulent MFA request due to an MFA bombing attack," says David Orth, KSL Capital Partners’ head of IT. "Users need continued training and support so that they report a flood of MFA requests instead of answering/approving the requests to get them to stop – not realizing they may have just given unauthorized access to ‘bad guys.’"
While adopting MFA does not close the door on every threat to accounts, it does make it that much harder for hackers to gain access to your data. "A vast majority of incidents we respond to could have been prevented by MFA," says Spencer Lynch, managing director of cyber security for Aon's Cyber Solutions in EMEA.
"However, having MFA in itself is not enough," he adds. "As businesses reevaluate hybrid work and continue to enable a remote workforce, the question on leaders’ minds should not be whether they have implemented MFA but rather how to ensure effective MFA."
Case Study: Financial Controls can Help to Mitigate the Effects of MFA Fatigue
Upon investigation into suspicious emails from a global management consulting firm’s employee’s account, Aon found that an external threat actor had gained access to the MFA-enabled account on multiple occasions – a classic case of Business Email Compromise.
An interview with the custodian and review of log data revealed that because the employee in question received repeated MFA prompts through the day as he accessed various resources, he had grown accustomed to choosing ‘Yes’, doing so regularly out of habit.
Once the attacker got access, he realized the compromised employee was from the finance department and routinely wired money in and out of the company’s corporate account. The attacker tried to send a request for funds to be sent to a new account – a common modus operandi.
Thankfully, the consulting firm had robust financial controls in place that required multiple levels of approval to set up new accounts and make payments. This not only blocked the transaction, but also caused the firm to detect the attack.
Securing Your Accounts, Devices, and Data
As attacks evolve, so should your defense. “Business leaders need to adopt a ‘defend forward’ approach to cyber risk to help build cyber security that allows their organization to scale and keep pace with the challenge,” says Ansbach.
Companies can take various approaches to help mitigate the emerging risk of MFA bypass, including the following:
- Implement hardware MFA/FIDO2 authentication (e.g.,Yubikeys)
- Enable “number matching” on authenticator apps
- Set limits on the number of MFA push notifications
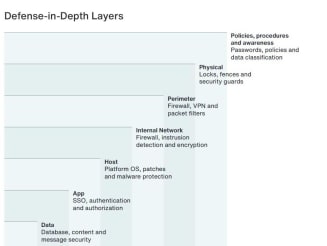
- Deploy Defense in Depth strategy – set up defenses at the perimeter of the environment as well as detections within the network to alert your organization quickly if MFA is successfully bypassed
- Provide training to all users, ensuring type of actions that require MFA authentication is fully understood
- Reduce/transfer risk through cyber insurance – many insurers and third-party vendors are starting to require MFA
- Consider the use of "Impossible Travel" remote access features to prevent authentication from locations that are unlikely to be legitimate
Source: Wallarm
Cyber criminals are nimble, forward-thinking, and persistent, and may still figure out how to get the best of your layered system; but without MFA they’re only one factor away from access. “No matter how many multiple layers an organization employs, continued vigilance and threat awareness is a constant,” says Morgan.
1 Kaspersky: Quick, cheap and dangerous – how scammers are creating thousands of fake pages using phishing kits
2 OKTA: How COVID-19 Is Changing the Way We Work – Zoom Boom + MFA is the Way
3 European Union Agency for Network and Information Security (ENISA): Guidelines for SMEs on the security of personal data processing
4 CyberEdge: 2022 Cyberthreat Defense Report
5 The National: Top 12 cyber crime trends to watch for in 2023
General Disclaimer
The information contained herein and the statements expressed are of a general nature and are not intended to address the circumstances of any particular individual or entity. Although we endeavor to provide accurate and timely information and use sources we consider reliable, there can be no guarantee that such information is accurate as of the date it is received or that it will continue to be accurate in the future. No one should act on such information without appropriate professional advice after a thorough examination of the particular situation.
Terms of Use
The contents herein may not be reproduced, reused, reprinted or redistributed without the expressed written consent of Aon, unless otherwise authorized by Aon. To use information contained herein, please write to our team.
43%
of IT security decision-makers and practitioners worldwide do not have MFA deployed in their companies
Source: CyberEdge’s 2022 Cyberthreat Defense Report
Insights for HR
This collection is a set of featured articles.
Cyber Labs
Stay in the loop on today's most pressing cyber security matters.
Environmental, Social and Governance Insights
Explore Aon's latest environmental social and governance (ESG) insights.
Insights for HR
Explore our hand-picked insights for human resources professionals.
Navigating Volatility
How do businesses navigate their way through new forms of volatility and make decisions that protect and grow their organizations?





















